CIS 527
Lecture 5 - Permissions & Security
Windows Updates
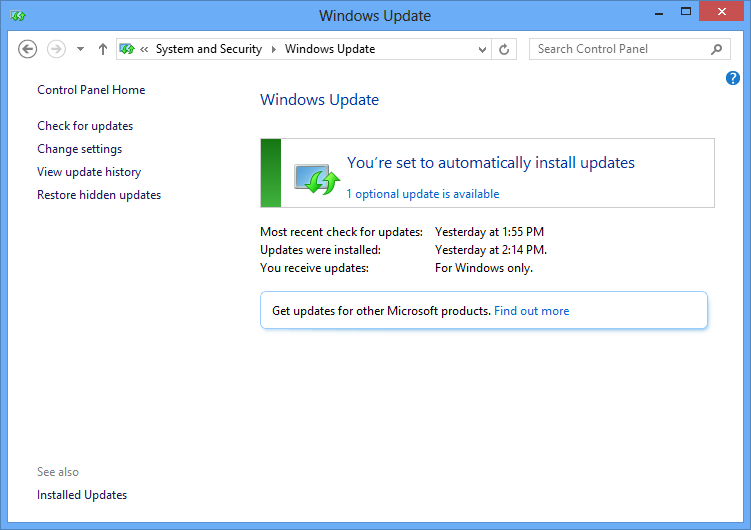
Ubuntu Updates
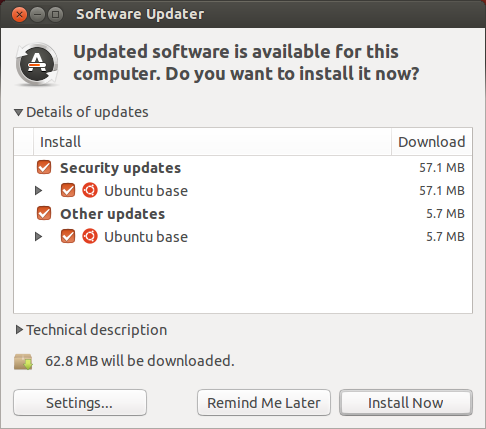
Advanced Packaging Tool - APT
- apt-get install <package>
- apt-get build-dep <package>
- auto-apt run <command_string>
- apt-get update
- apt-get upgrade
- dpkg-reconfigure <package>
- apt-get remove <package>
- apt-get purge <package>
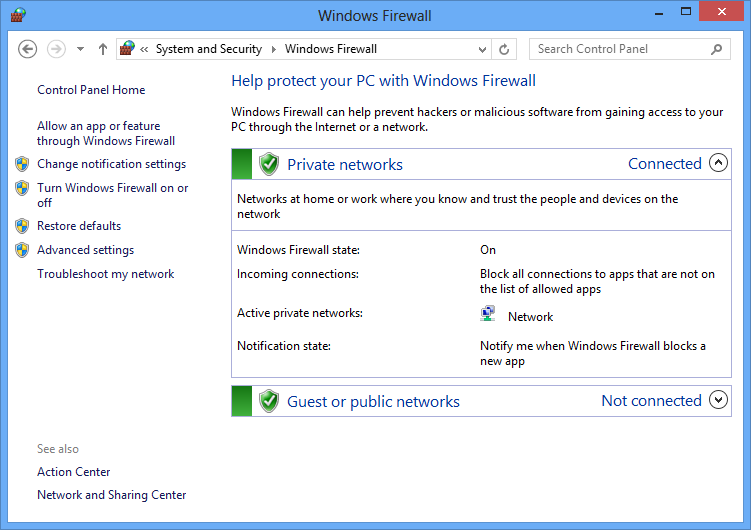
Windows Firewall
Ubuntu Firewall (UFW)
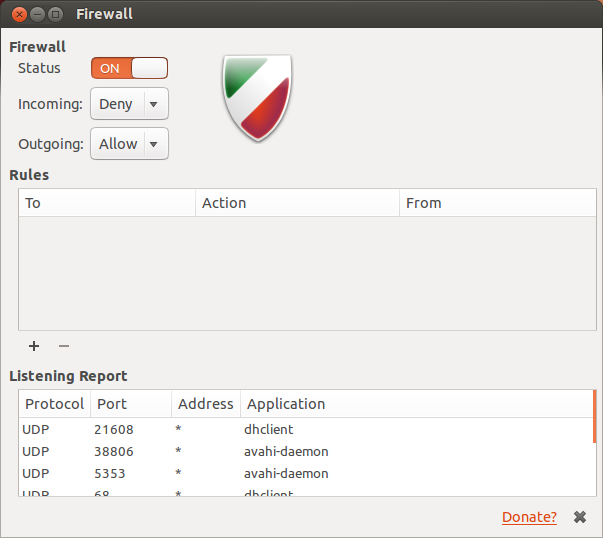
Uncomplicated Firewall (UFW)
- ufw allow <port>
- ufw allow <port>/tcp
- ufw deny <port>
- ufw delete <original_rule>
- ufw allow <service_name>
- ufw allow from <ip_address> to <ip_address> port <port>
Iptables
- iptables -A INPUT --dport <port> -j ACCEPT
- iptables -A INPUT -p tcp --dport <port> -j ACCEPT
- iptables -A INPUT -p tcp --dport <port> -j REJECT
- Must save and restore rules on restart
Trend Micro AntiVirus
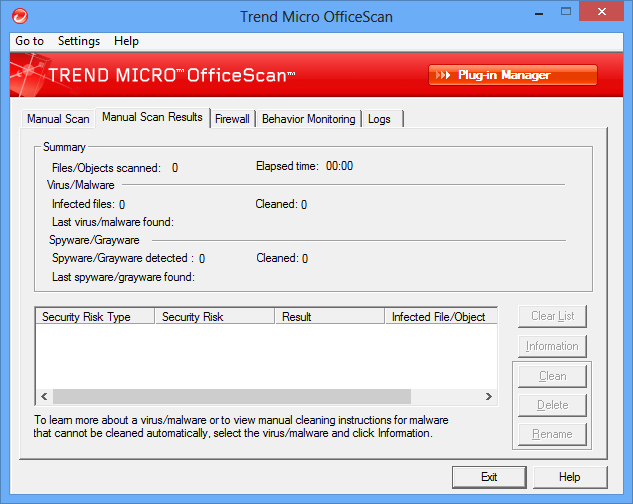
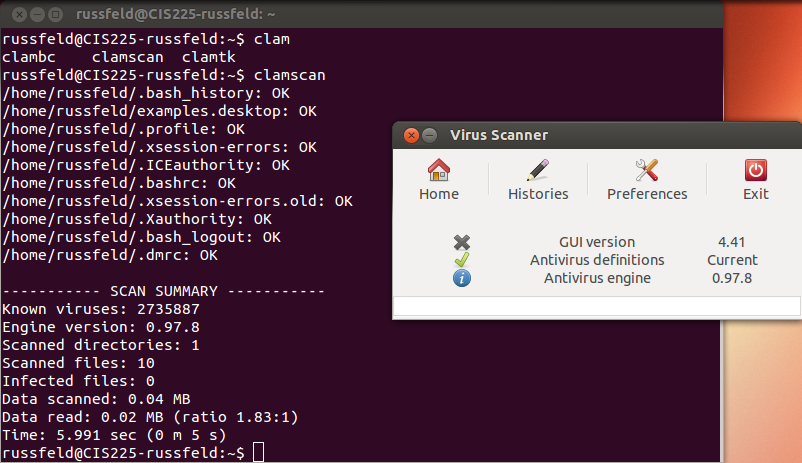
ClamAV
Software Evaluation
- You work for an insurance company
- You receive a request to install unknown software on a system
- How do you ensure the software is safe to use?
- What are the risks?
Reputable Sources
- Verify the software comes from a well-known source
- Do they create other programs?
- Have they been reviewed?
Support Offerings
- What does the company offer for support?
- Is there an active user community?
- Are there common problems reports in forums
- Can you request in-person help if major issues arise?
Company History & Coding
- Does the company have a history of software issues?
- Do they have proper coding practices in place (code reviews, secure processes, etc.)?
- Are they frequently issuing security fixes? (Is that a good thing or a bad thing?)
Code Signing
- Similar to Web Security certificates
- Allows publishers to verify that the software came from them
- Can be subverted if the root certificate is compromised
- Ex: Windows WQHL Drivers
Checksum Verification
- Many sites provide checksums for software that can be downloaded
- Verifying the checksum ensures that it hasn't been changed or corrupted
Extra Software
- Many less-reputable programs install extra software (toolbars, adware, malware, etc.)
- Those programs may be MUCH worse than the actual program installed
- Read installers CAREFULLY!
- Use system monitoring tools to see what changes during installation
Data Storage & Access
- Where does the program store data?
- Is it encrypted or plain-text?
- What data does it request?
- How does it use the data?
Monitor Network
- Once software is installed, it usually has full network access
- Use tools such as TCPView and netstat to monitor network connections
- Look for connections to random servers or large data throughput
Network Usage
- What data does it send through the network?
- Is the data encrypted or plain-text?
- What protocols and ports does it use?
- Read the license agreement; it may surprise you
- Make sure you understand EVERYTHING that it covers
- Acknowledge the rights you are giving away
Use Testbeds
- Test the software on a variety of systems
- Spend time testing (don't just install and review)
- Test on a variety of systems and configurations
- Roll out in stages in large organizations
Install Updates
- Install updates provided by the manufacturer
- Test updates before installing
- Monitor the system and report bugs
Permissions
- Determines which users can read/write files
- Based on user and group memberships
- Helps prevent unwanted access to files
Windows Permissions
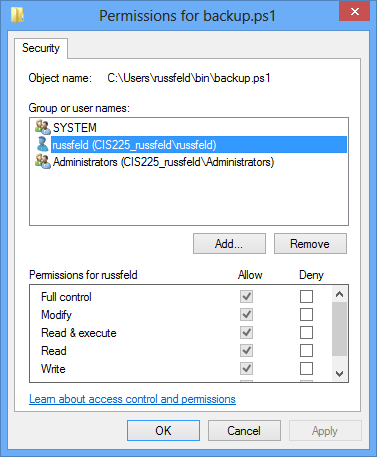
Windows Permissions
- Full Control - Can take ownership & change permissions
- Modify - Read/Write/Change/Delete
- Read & Execute
- List Folder Contents - Folders Only
- Read - Access files
- Write - Modify files
Ubuntu Permissions
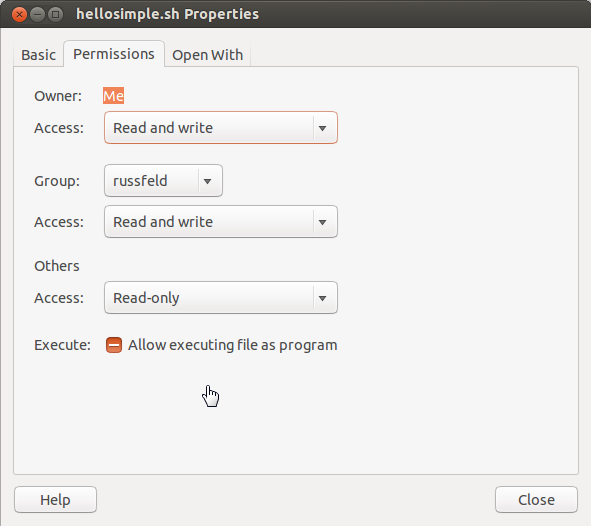
Ubuntu Permissions
- 3 classes: User, Group, Others
- 3 rights:
- Read - Can read contents
- Write - Can create/modify/delete
- Execute - Can run programs/scripts
Modifying Ubuntu Permissions
- chmod - Change permissions
- chmod [class][op][mode] file/folder
- chmod [octal_mode] filename/folder
- chown - Change User/Group (sudo)
- chown [user]:[group] filename/folder
- chgrp - Change Group (must own file)
- chgrp [group] filename/folder
Octal Modes
- R = 4, W = 2, X = 1
- Sum the numbers to get mode
- 660 = rw-rw----
- 644 = rw-r--r--
- 700 = rwx------
- chmod 644 <filename>
Assignments
- Lab 1 - Secure Workstations - Due Sunday, Feb 9th by 12:30 PM
- Build secure Windows & Linux using VMWare Workstation
- Turn in:
- CIS Transient Storage
- via Storage Media in class Monday Feb 9th