CIS 527
Lecture 26 - System Monitoring
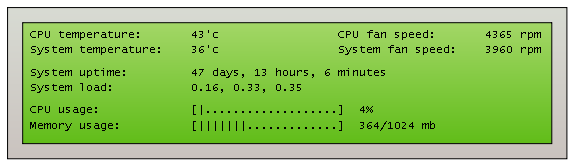
Processor Usage
- Windows - Resource Monitor, Process Explorer
- Ubuntu - top, vmstat, ps
Memory Usage
- Windows - Resource Monitor, Process Explorer
- Ubuntu - free
Disk Usage
- Windows - Disk Management, Windirstat
- Ubuntu - du, df, iostat
Network Usage
- Windows - Resource Monitor, TCPView
- Ubuntu - netstat, ss, tcptrack
Inventory
Every good system administrator should keep an up-to-date inventory of all systems being managed
WinAudit
OCS-NG Demo Site
Simple Network Management Protocol (SNMP)
- Read data from systems via network
- Some system settings can be changed
- Typically present on networking devices
- GOOD: Easy to read data on many systems
- BAD: Must be properly configured or can be security issue
Enterprise Solutions
- Zabbix
- Hyperic
- Munin
- Cacti
- Nagios
- Ganglia
Features? Downsides? Would you use?
Assignments
- Presentations Monday & Wednesday next week!
- Lab Help Session Fridays 9 - 10 AM!
- Lab 7 - Backups & Monitoring - Due Sunday, May 11th by 11:59 PM
- Create Backup & Monitoring Strategies
- Turn in via K-State Online
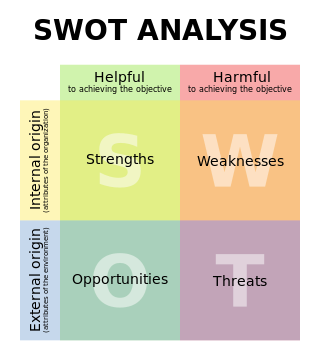
SWOT Analysis
- Choose an IT organization familiar to you
- Your home network
- A work or school network
- Local or family organizations
- A fictional (but well defined) system
SWOT Analysis
- Internal Strengths - things that you are good at
- Internal Weaknesses - things that you are bad at
SWOT Analysis
- External Opportunities - things you can exploit to get better
- External Threats - things that could exploit you and make you worse
Presentation
- Overview of the IT org (~1-2 min)
- Internal Strengths (~2 min)
- Internal Weaknesses (~2 min)
- External Opportunities (~2 min)
- External Threats (~2 min)
- Suggestions to Improve based on SWOT Results (~2-4 min)
- Questions (~2 min)