Your browser doesn't support the features required by impress.js, so you are presented with a simplified version of this presentation.
For the best experience please use the latest Chrome, Safari or Firefox browser.
Jeff Bezos in front of an 1890s electric generator from a Belgian beer brewery
Image Source: Information Week
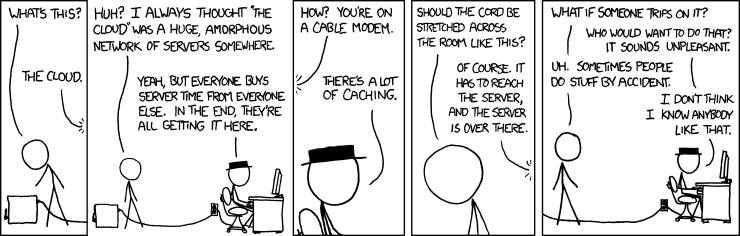
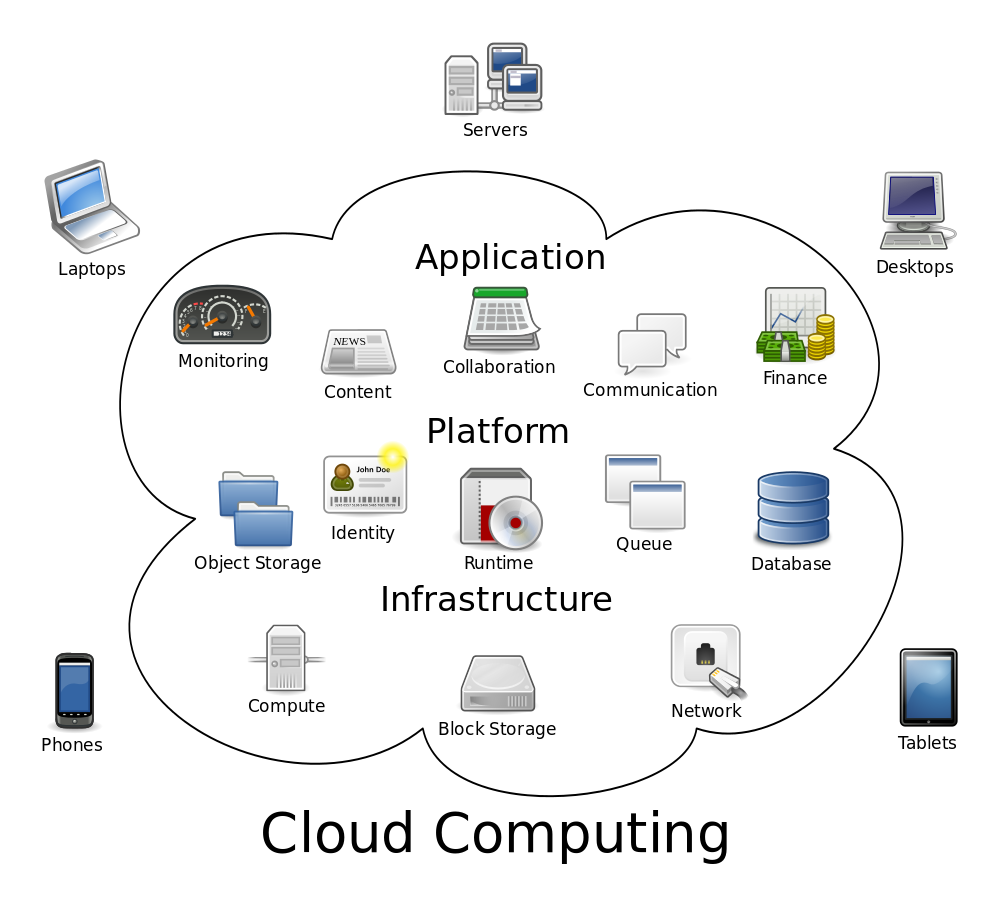
Cloud Computing
- Originated in "time sharing" in the 1950ss
- Early network diagrams used a cloud for unknown networks
- Businesses started using VPNs in the 1990s
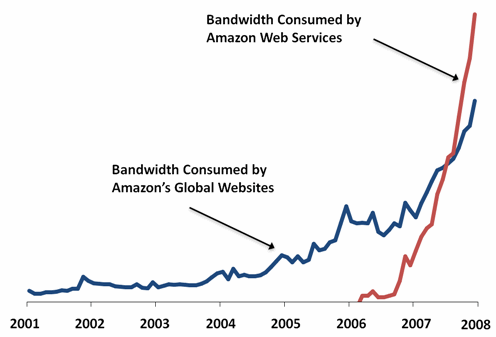
- Popularized in 2006 by Amazon's Elastic Compute Cloud (EC2)
Virtual Private Networks
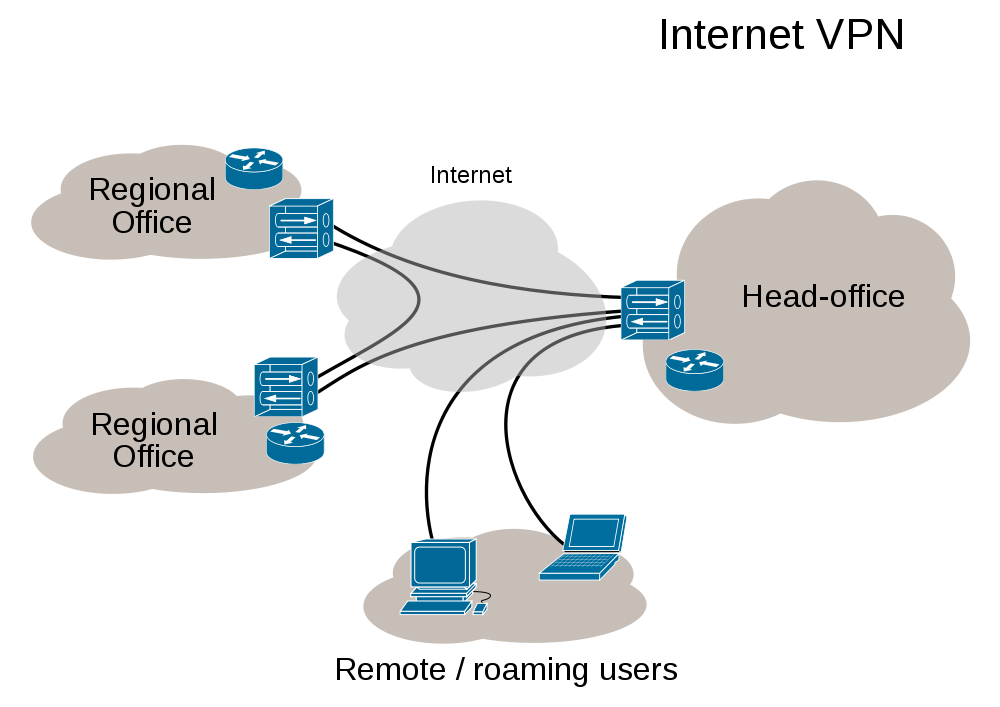
Image Source: Wikipedia
Service Oriented Architecture
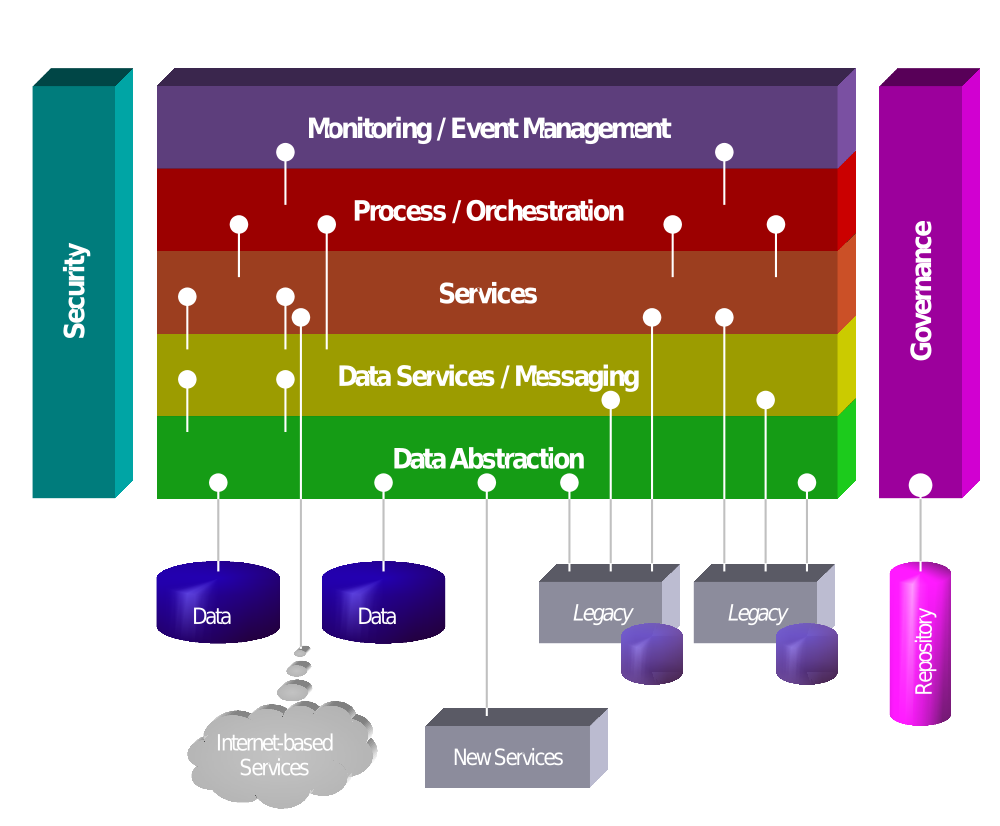
Image Source: Wikipedia
Cloud Computing Characteristics
According to NIST
- On-demand self-service
- Broad network access
- Resource Pooling
- Rapid elasticity
- Measured Service
What makes Cloud Computing Work
- Location Independent
- Multi-tenancy (share costs)
- Reliability
- Scalability / Elasticity
- Security
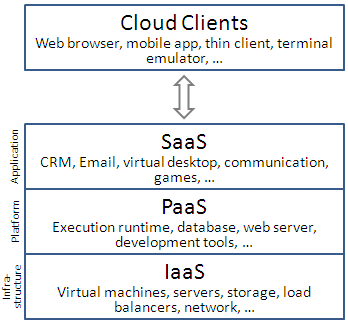
Service Models
- Infrastructure as a Service (IaaS)
- Platform as a Service (PaaS)
- Software as a Service (Saas)
- Data as a Service (Daas)
- <Anything> as a Service
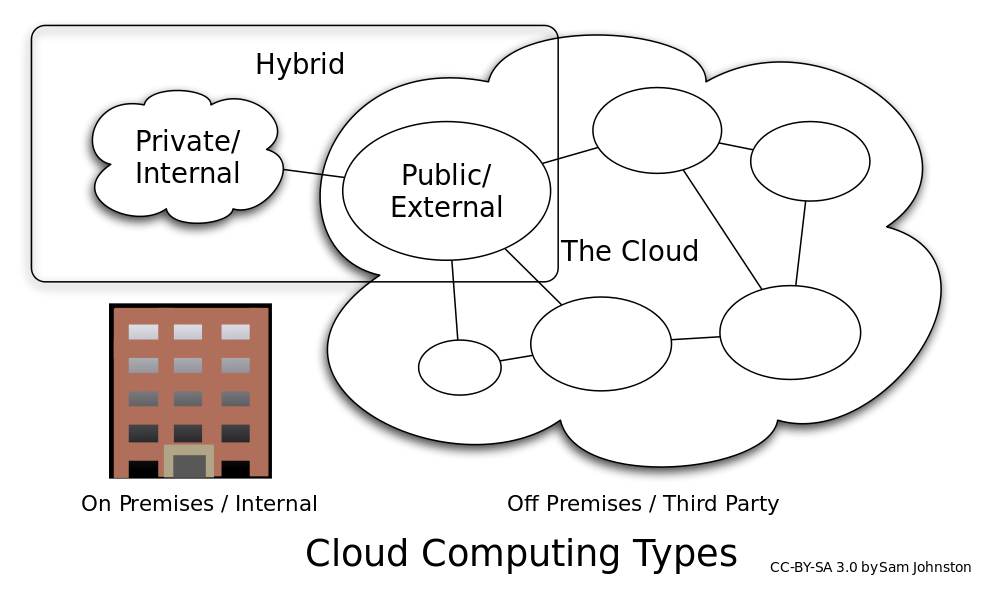
Deployment Models
- Private Cloud
- Public Cloud
- Hybrid Cloud
- Community Cloud
- Distributed Cloud
- Intercloud/Multicloud
Big Players in the Cloud
- Amazon Web Services
- Microsoft Azure
- IBM SmartCloud
- Rackspace Cloud
- Heroku
- Google
- HP
Cloud Threats
- Insecure Interfaces & APIs - 29%
- Data Loss & Leakage - 25%
- Hardware Failure - 10%
- Legal Data Ownership
- Lack of Physical Control
- Big Targets for Hackers
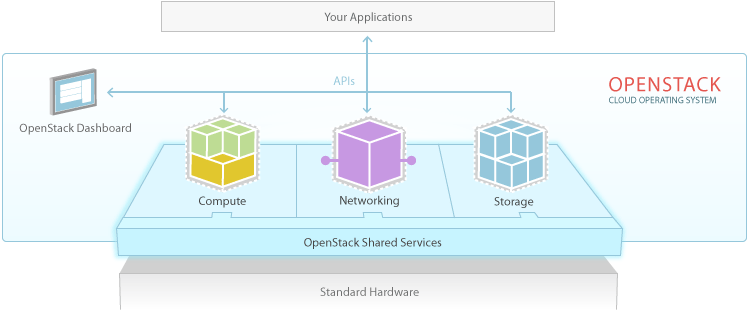
Open Stack
- Started in 2010 by Rackspace Hosting & NASA
- Open source project to help companies with cloud computing
- Includes many components needed for cloud computing
DigitalOcean
- Cloud Infrastructure Provider
- Started Aug 2011, 100K droplets by March 2013
- Very Active Community
- SSD-only cloud (FAST!)
SSH Keys
- Uses RSA Public-Private Keys for authentication
- Much more secure than plain passwords
- Can be used for automatic logins as well
Network Time Protocol
- Allows server clocks to synchronize via the network
- Useful for helping computer verify the timeliness of messages
- Also used to invalidate old credentials and certificates
Swapfiles
- What happens when a computer runs out of RAM?
Swapfiles
- What happens when a computer runs out of RAM?
- It stores excess "pages" of RAM data on the hard drive
- Called "paging" or "swapping"
- Very important on servers to help prevent crashes due to lack of memory
Apache/PHP/SSL
- Common web server setup on the cloud
- SSL helps protect and encrypt data
- Self-signed certificates are good for testing
- Paid certificates should be used when deploying
Assignments
- Lab 9 - The Cloud
Due 11/14 12:30 PM