CIS 225
Lecture 11: User Management
User Accounts
- Allows multiple people to share resources
- Each user can have different permissions
- Aids in auditing (who did what)
- Protects system from unauthorized use
Authentication vs. Authorization
- Authentication - Confirming a user is who he or she claims to be (logging in)
- Authorization - Allow an authenticated user access to specific resources
- Authentication DOES NOT IMPLY Authorization
Authentication Methods
One or more of the following factors
- Ownership factors - something user has
- Knowledge factors - something user knows
- Inheritance factors - something user is or does
Authorization Methods
- Security Policies
- Access Control Lists (ACL)
User Identification
- Operating systems refer to users by a unique identifier
- Linux: user identifier (UID)
- Windows: security identifier (SID)
- This allows user to change usernames without affecting the account
User Account Information
- UID / SID
- Username
- Password
- Home directory
- Group(s)
Groups
- List of user accounts
- Aid in assigning access to users
- Each user may be a part of one or many groups
- Unique identifier
- Linux: group identifier (GID)
- Windows: security identifier (SID)
Windows 8 Accounts
Control Panel
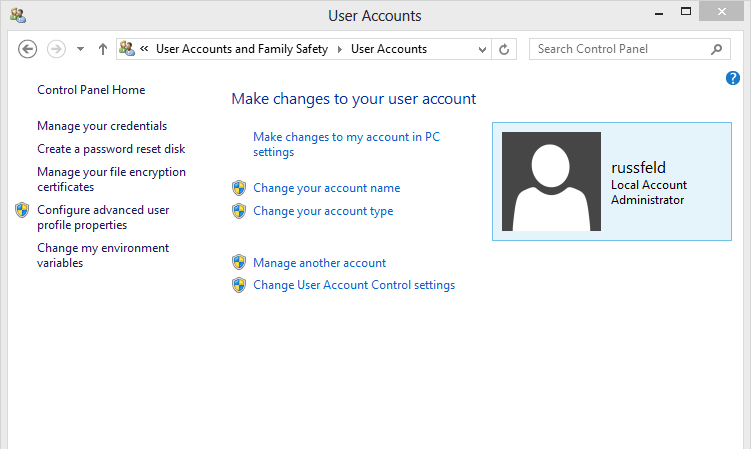
Windows 8 Accounts
Computer Management
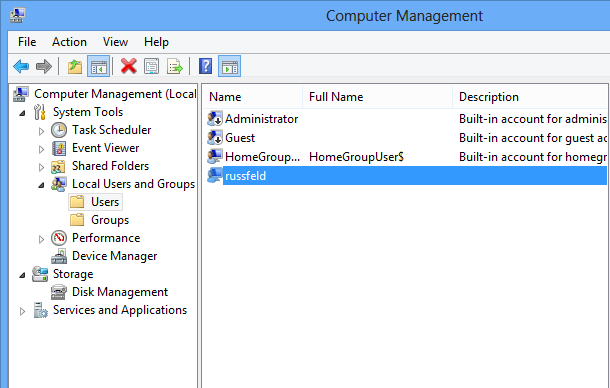
Windows 8 Default Accounts
- Administrator
- Access to everything
- Cannot be deleted
- Disabled by default
- Has no password by default
- Guest
- Limited access
- Disabled by default
Windows 8 Pseudo Accounts
- LocalSystem - system-level tasks & services
- LocalService - fewer rights than LocalSystem
- NetworkService - fewer rights than LocalService, but allows network access
Windows 8 Default Groups
- Administrators - complete access
- Event Log Readers - read event logs
- Guests - access system only
- Power Users - not used
- Remote Desktop Users - log on remotely
- Users - normal users
Many others, refer to documentation
User Account Control
- Protects the system from unwanted changes
- Allows administrators to run commands from a non-administrator account
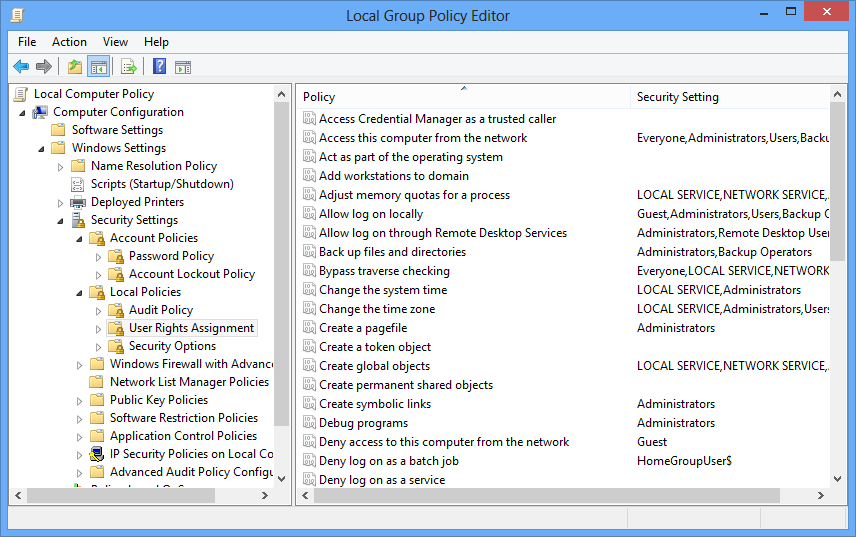
Local Group Policy Editor
WIN+R - gpedit.msc
Ubuntu Account Types
- Super User (root)
- Complete control
- Disabled by default
- UID = 0; GID = 0
- Regular User
- User who can log on to the system
- System User
- Used by programs and services to access the system
Ubuntu Accounts
Regular Users:
- UID: starting at 1000 and up
- Each account has a private group created with matching GID
Ubuntu Accounts
System Settings
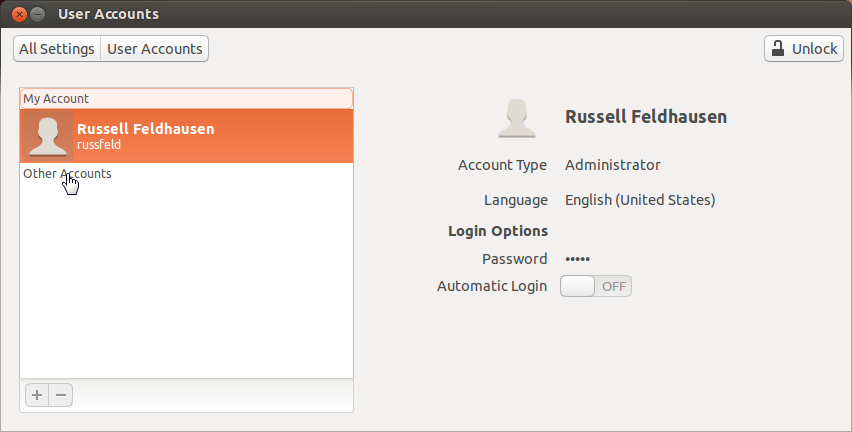
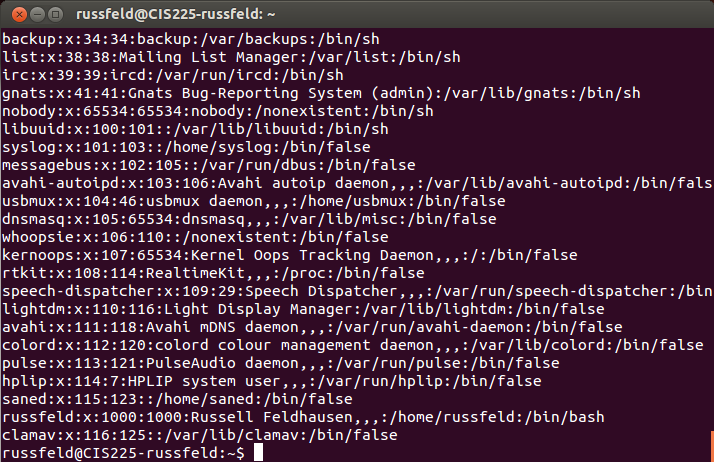
/etc/passwd
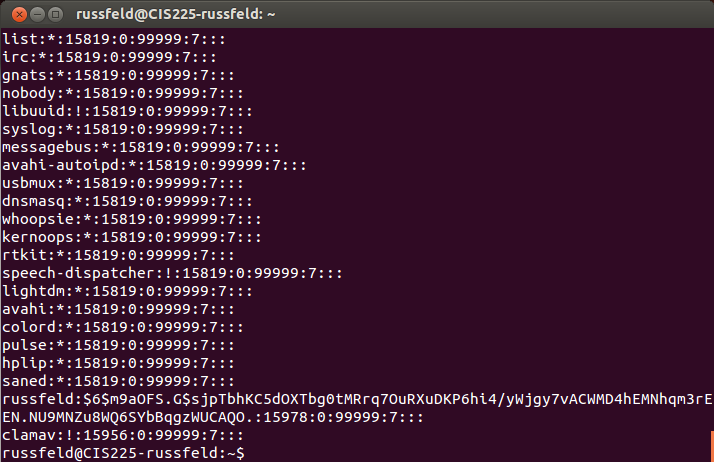
/etc/shadow
Commands
- groupadd - add a group
- groupdel - remove a group
- groupmod - modify group
- gpasswd - change group administrator or password
- useradd - add a user
- userdel - remove a user
- usermod - modify a user
- passwd - change password
sudo
- Short for "super user do"
- Allows regular users to run commands as root
- User and rights listed in /etc/sudoers
- Add users to the "sudo" or "admin" group to give them access
Reading
- Windows 8 Book - Chapter 13
- Ubuntu Unleashed - Chapter 10
Assignments
- Lab 5 - User & File Management: Due 10/13 @ 11:30 AM
Exam Results
- Max - 82/82, Min - 56.5/82
- Avg - 71 (86%), Median - 70 (86%)
- MC - Avg 21/24, Median 21/24