Your browser doesn't support the features required by impress.js, so you are presented with a simplified version of this presentation.
For the best experience please use the latest Chrome, Safari or Firefox browser.
How can we keep our data secure?
Authentication
- Ownership Factors - something the user has
- Knowledge Factors - something the user knows
- Inherence Factors - something the user is
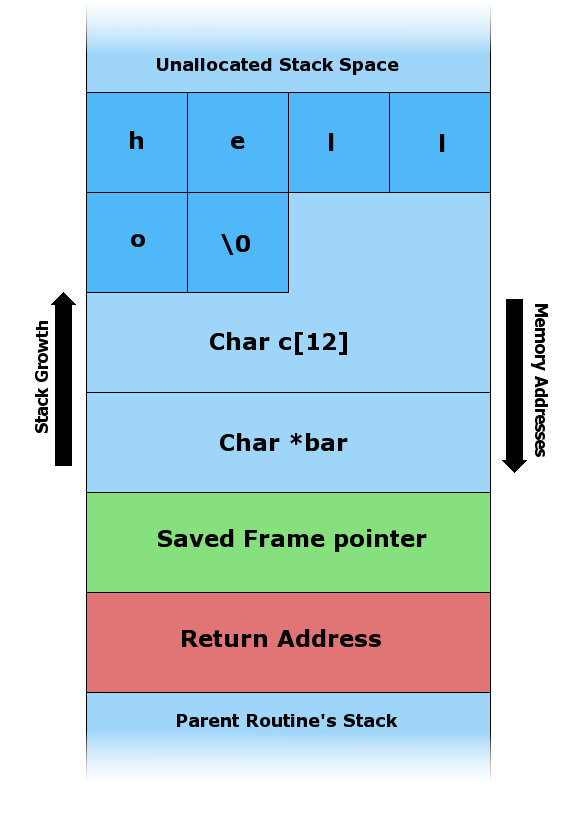
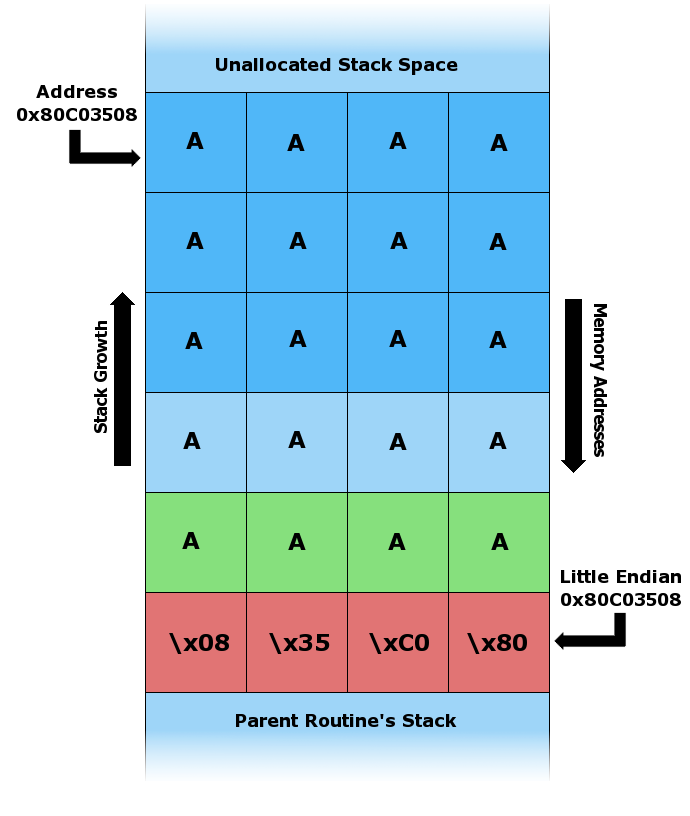
Passwords
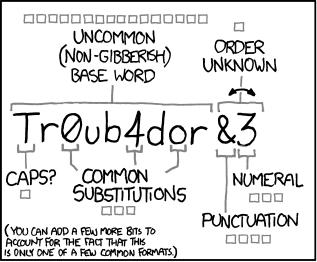
Image Source: XKCD
Cracking Passwords - Brute Force
- aaaaaa
- aaaaab
- aaaaac
- aaaaad
- aaaaae
- aaaaaf
- aaaaag
- aaaaah
- aaaaai
- aaaaaj
- aaaaak
- aaaaal
- aaaaam
- aaaaan
- aaaaao
- aaaaap
- aaaaaq
- aaaaar
- aaaaas
- aaaaat
- aaaaau
Cracking Passwords - Lookup Table
- password
- 123456
- 12345678
- abc123
- qwerty
- monkey
- letmein
- dragon
- 111111
- baseball
- iloveyou
- trustno1
- 1234567
- sunshine
- master
- 123123
- welcome
- shadow
- ashley
- football
- jesus
Source: Gizmodo
Rainbow Tables
Password Entropy

Image Source: XKCD
Password Entropy
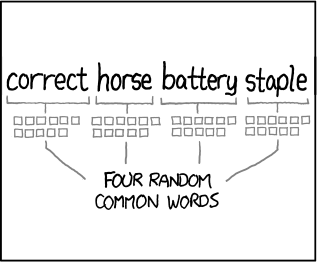
Image Source: XKCD
Password Entropy
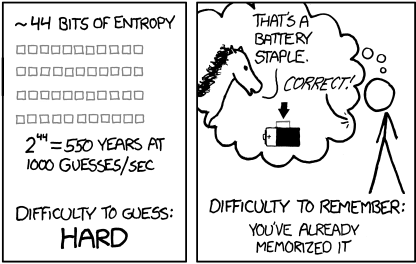
Image Source: XKCD
Storing Passwords Securely
Store the password itself
- Needed to compromise: database access
- Accounts compromised: all
- Relative ease: simple
Storing Passwords Securely
Encrypt all passwords with a key
- Needed to compromise: database & key (or lookup table)
- Accounts compromised: all
- Relative ease: medium
Password Salt
- Random data added to a password before hashing
- Protects against dictionary and rainbow table attacks
- Ensures the password is long enough to be hard to crack
Storing Passwords Securely
Encrypt all passwords with a global salt value
- Needed to compromise: database, encryption key & salt value
- Accounts compromised: all
- Relative ease: harder
Storing Passwords Securely
Encrypt all passwords with a unique salt value
- Needed to compromise: database, encryption key & salt value
- Accounts compromised: one at a time
- Relative ease: really hard
Social Engineering
Using techniques to compromise a system by exploiting the users directly instead of the system's security

Image Source: Wikipedia
Pretexting

Image Source: Penetration Test Lab
Impersonation

Image Source: 1worder
Phishing
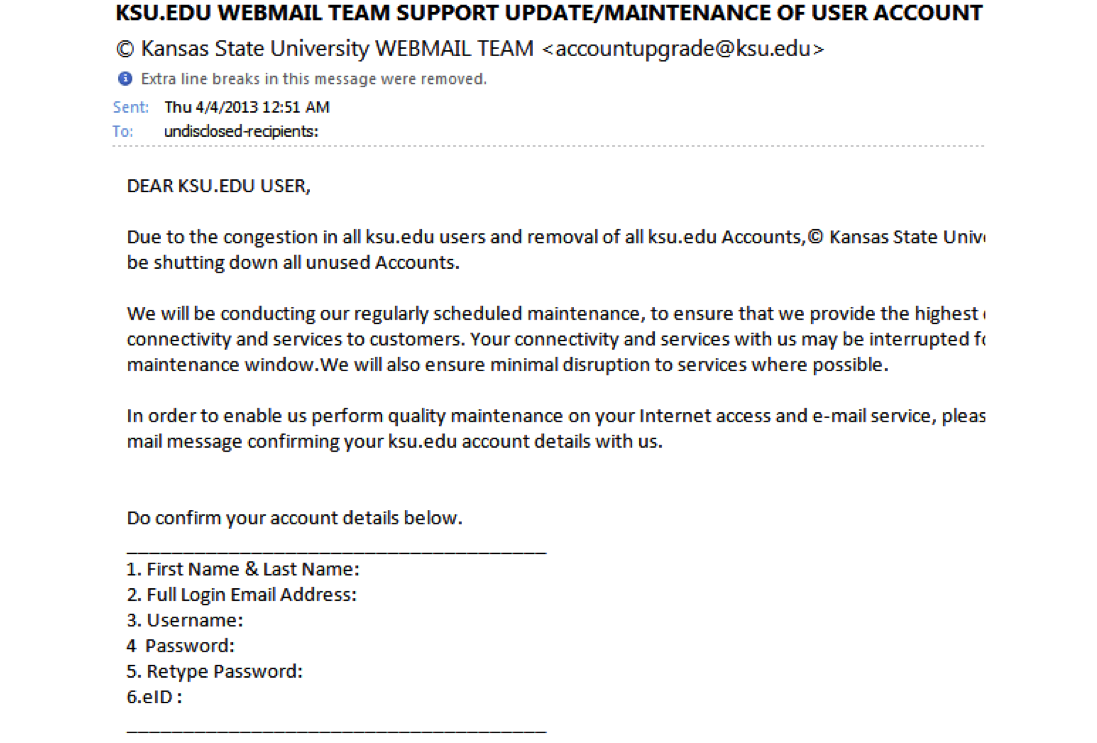
419 Scams
- Section 419 of Nigeria's Criminal Code
- Advance-fee fraud
- Pay a small sum of money now, they transfer a you large sum of money later
419 Scams
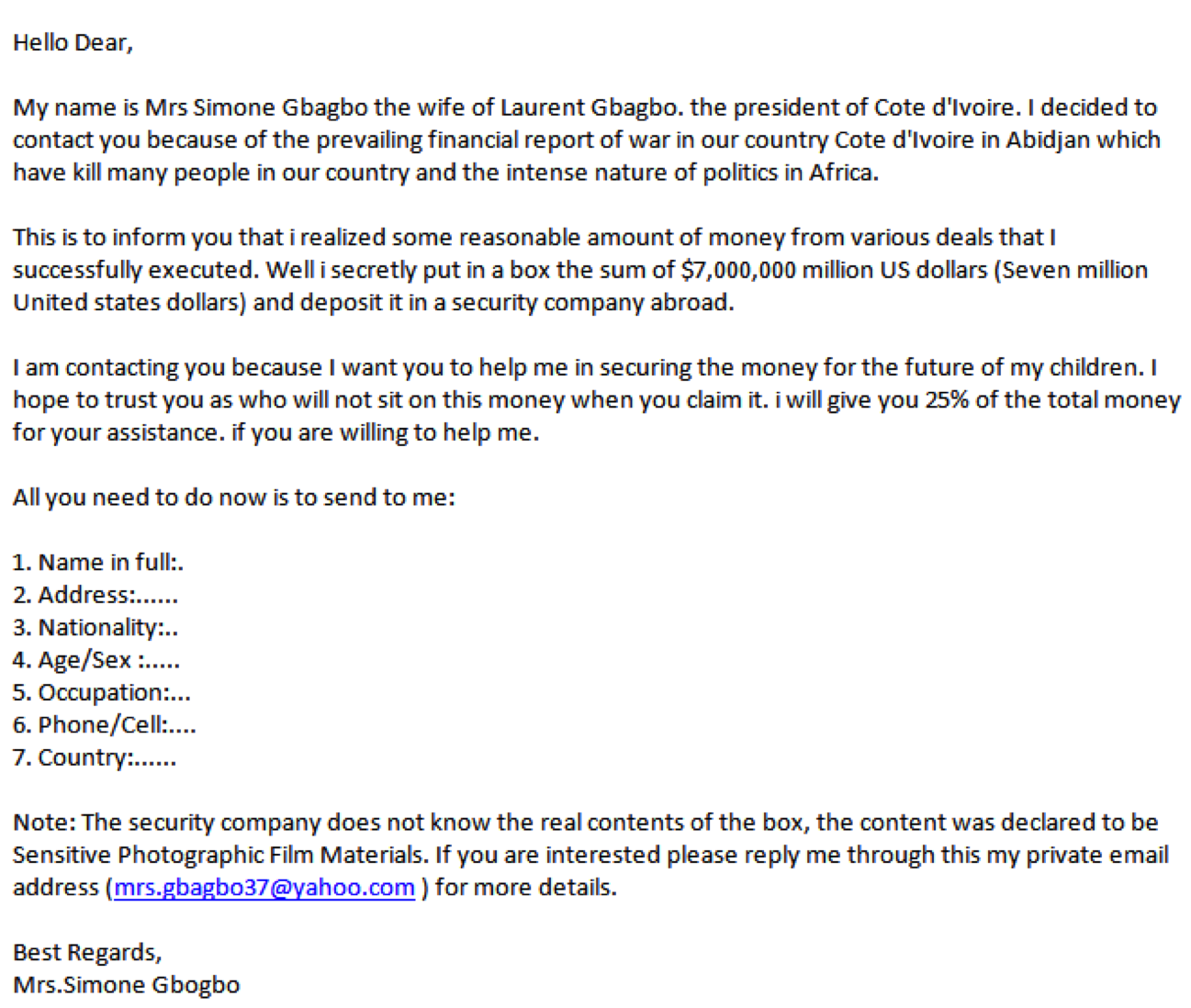
Threats
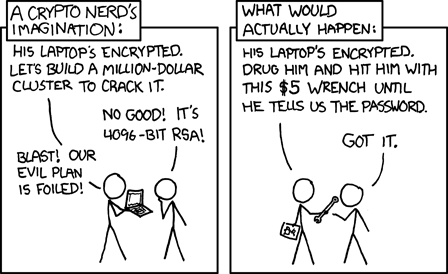
Image Source: XKCD
Combating Social Engineering
- User Training
- Security Protocols and Audits
- Always Questioning Everything
- Penetration Testing
- Properly Disposing of Garbage
Social Engineering in Practice
- "Capture the Flag" style contest held at DEF CON 21
- Contestant try to gain information about companies via the internet
- Using that information, they call the company and attempt to gain more information flags for points
Read the Report
Interception Attacks
Intercepting information in order to impersonate another entity or modify the information before it is received
Man in the Middle Attack
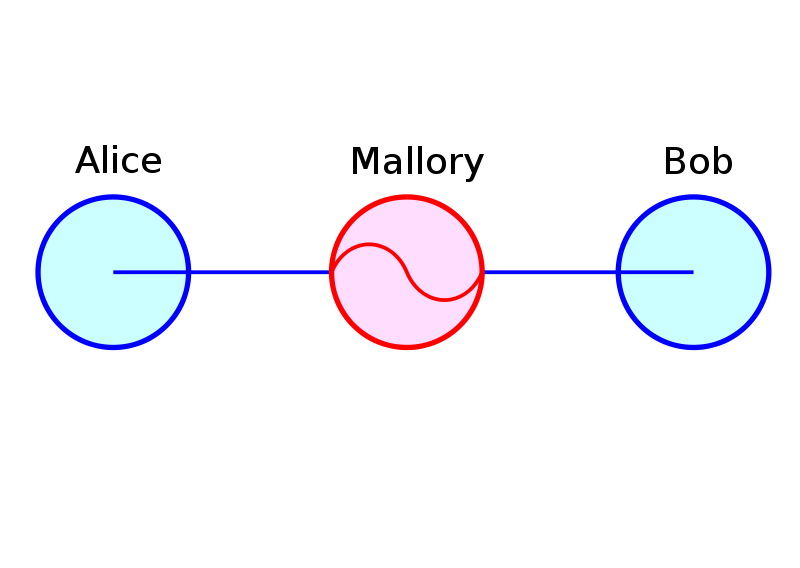
Image Source: Wikipedia
Man in the Browser Attack
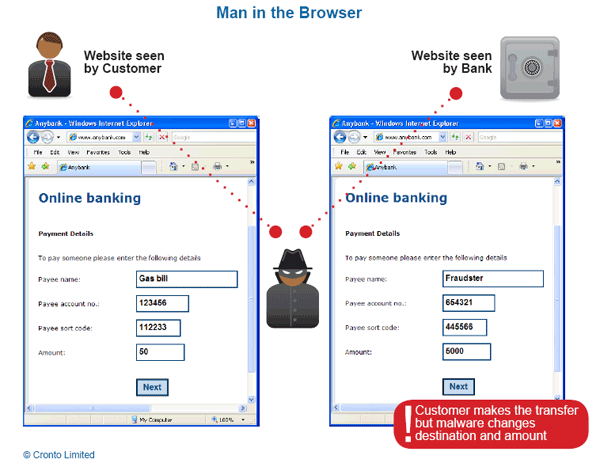
Image Source: Cronto
Malware
- Virus
- Ransomware
- Trojans / Worms
- Rootkits
- Keyloggers
- Spyware
- Adware
- Fake Security Software
Morris Worm
- Intended to study the size of the internet
- Caused machines to overload and fail
- Infected 6000 machines (10% of the internet)
- First major worm on the internet
Morris Worm
- Infected machines even if they were already infected 1 out of 7 times
- Many machines infected multiple times
- Creator sentenced to 3 years probation and paid $10,000 fine
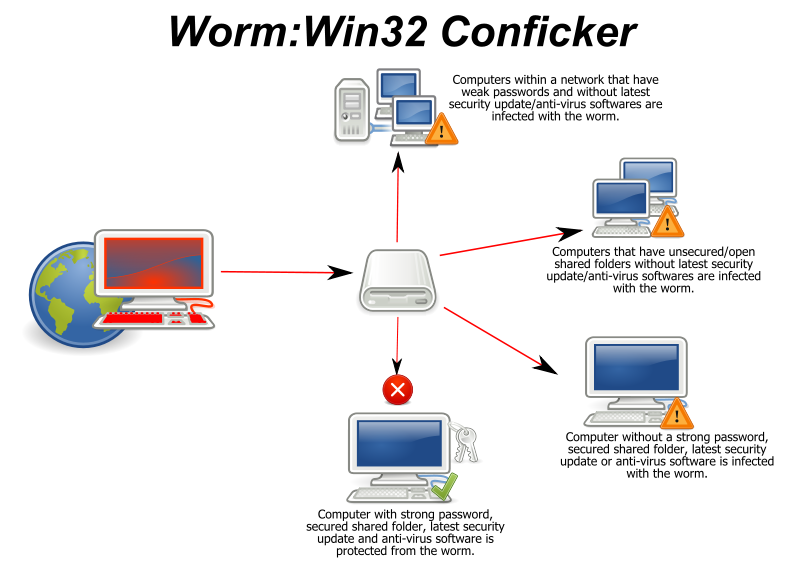
Conficker
- January 2009 - 9-15 million infected
- Fix released in October 2008, but 30% of PCs didn't have it installed by Jan 2009
- Mid 2011 - 1.7 million infected
- Many government and corporate networks infected
Stuxnet
- Designed to infect Siemens SCADA systems
- Only targets systems doing a very specific job
- Sends faulty data to the controller while presenting fake data to the user
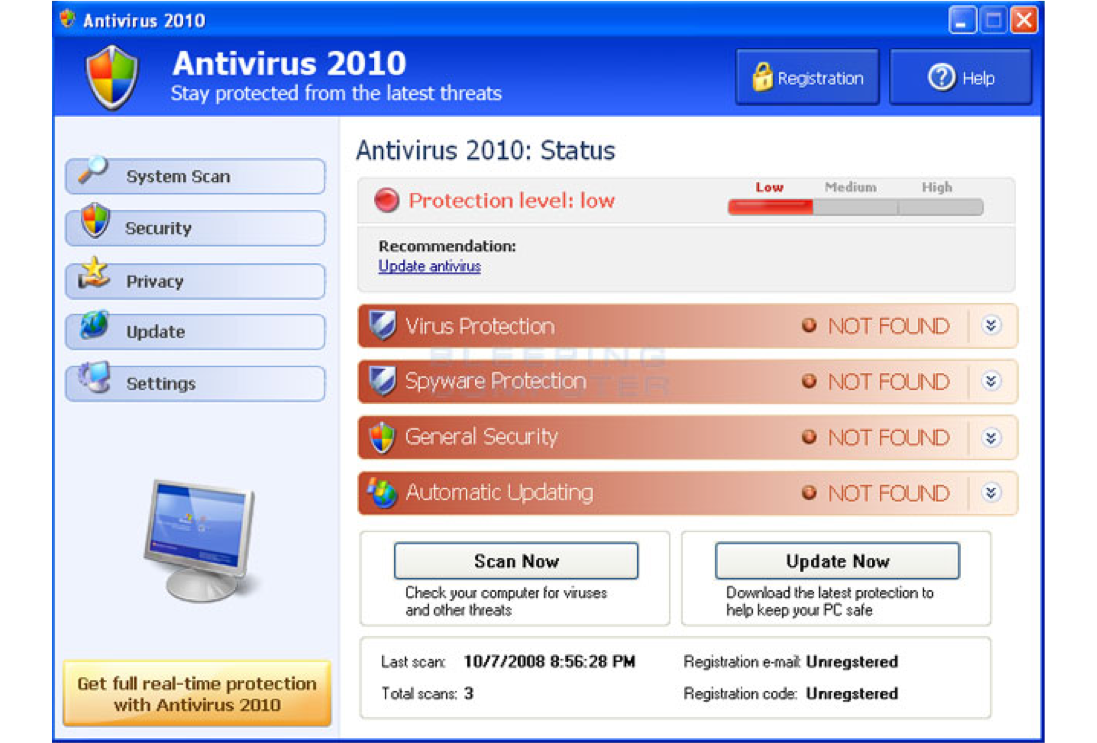
Fake AntiVirus
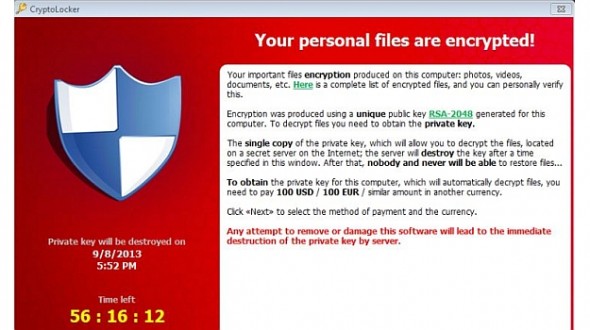
Cryptolocker
- Installed via a malicious email attachment
- Communicates with a server to receive a 2048-bit RSA public key
- Encrypts documents with public key and holds them ransom
- Current ransom: 2 bitcoins (~$300 at that time)
Software Attacks
Attacking vulnerabilities in the software running on a system to gain access or retrieve secure data
SQL Injection
Image Source: XKCD
SQL Injection
statement := "SELECT * FROM userinfo
WHERE id = " + a_variable + ";”
a_variable = “1”
SELECT * FROM userinfo WHERE id=1;
SQL Injection
statement := "SELECT * FROM userinfo
WHERE id = " + a_variable + ";”
a_variable = “1”
SELECT * FROM userinfo WHERE id=1;
statement := "SELECT * FROM userinfo
WHERE id = " + a_variable + ";”
a_variable = “1;DROP TABLE users;”
SELECT * FROM userinfo WHERE id=1;DROP TABLE users;
SQL Injection
http://books.example.com/showReview.php?ID=5
SELECT * FROM bookreviews WHERE ID = '5';
SQL Injection
http://books.example.com/showReview.php?ID=5
SELECT * FROM bookreviews WHERE ID = '5';
http://books.example.com/showReview.php?ID=5 AND 1=1
SELECT * FROM bookreviews WHERE ID = '5' AND '1'='1';
SQL Injection
http://books.example.com/showReview.php?ID=5
SELECT * FROM bookreviews WHERE ID = '5';
http://books.example.com/showReview.php?ID=5 AND 1=1
SELECT * FROM bookreviews WHERE ID = '5' AND '1'='1';
http://books.example.com/showReview.php?ID=5 AND substring(@@version,1,1)=4
SELECT * FROM bookreviews WHERE ID = '5' AND substring(@@version,1,1)=4;
Social Activism / Hactivism

Image Source: Wikipedia
Discussion
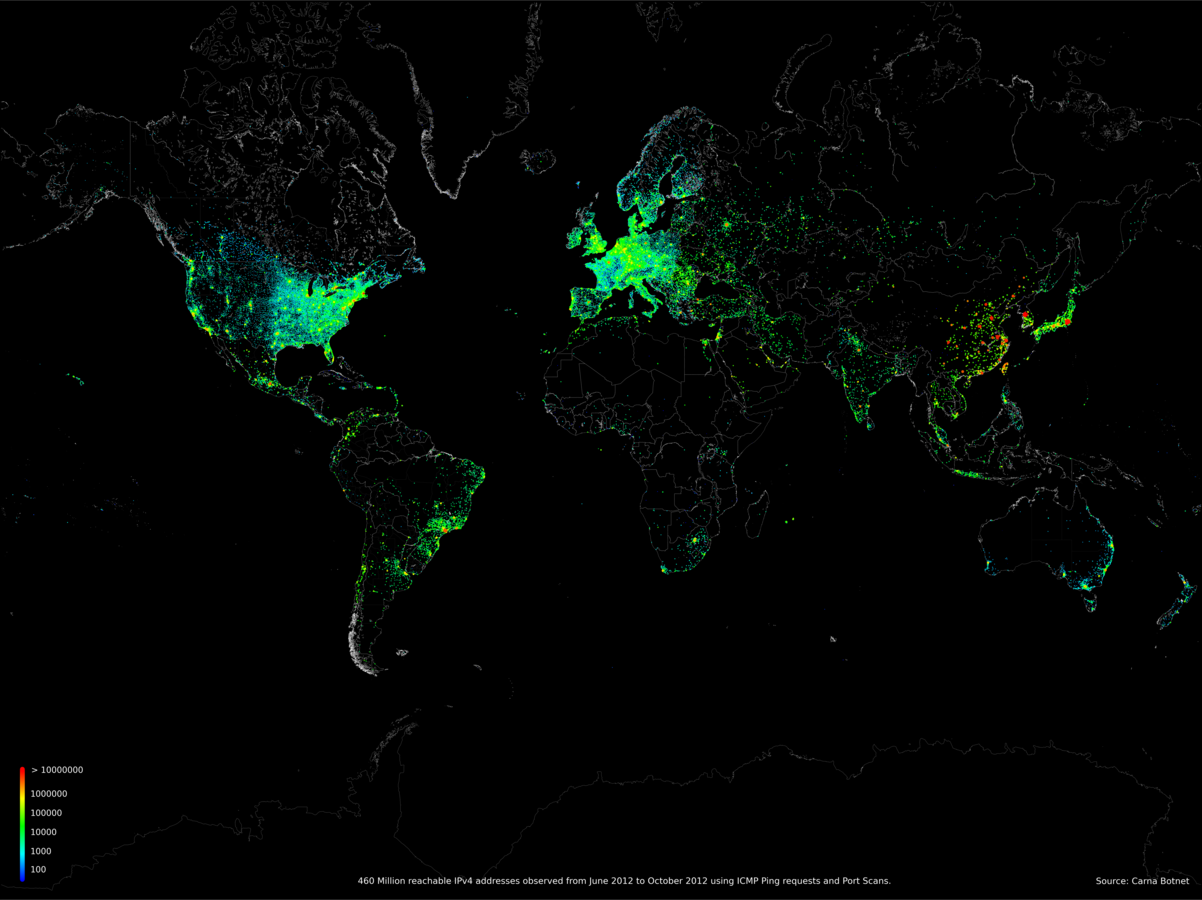
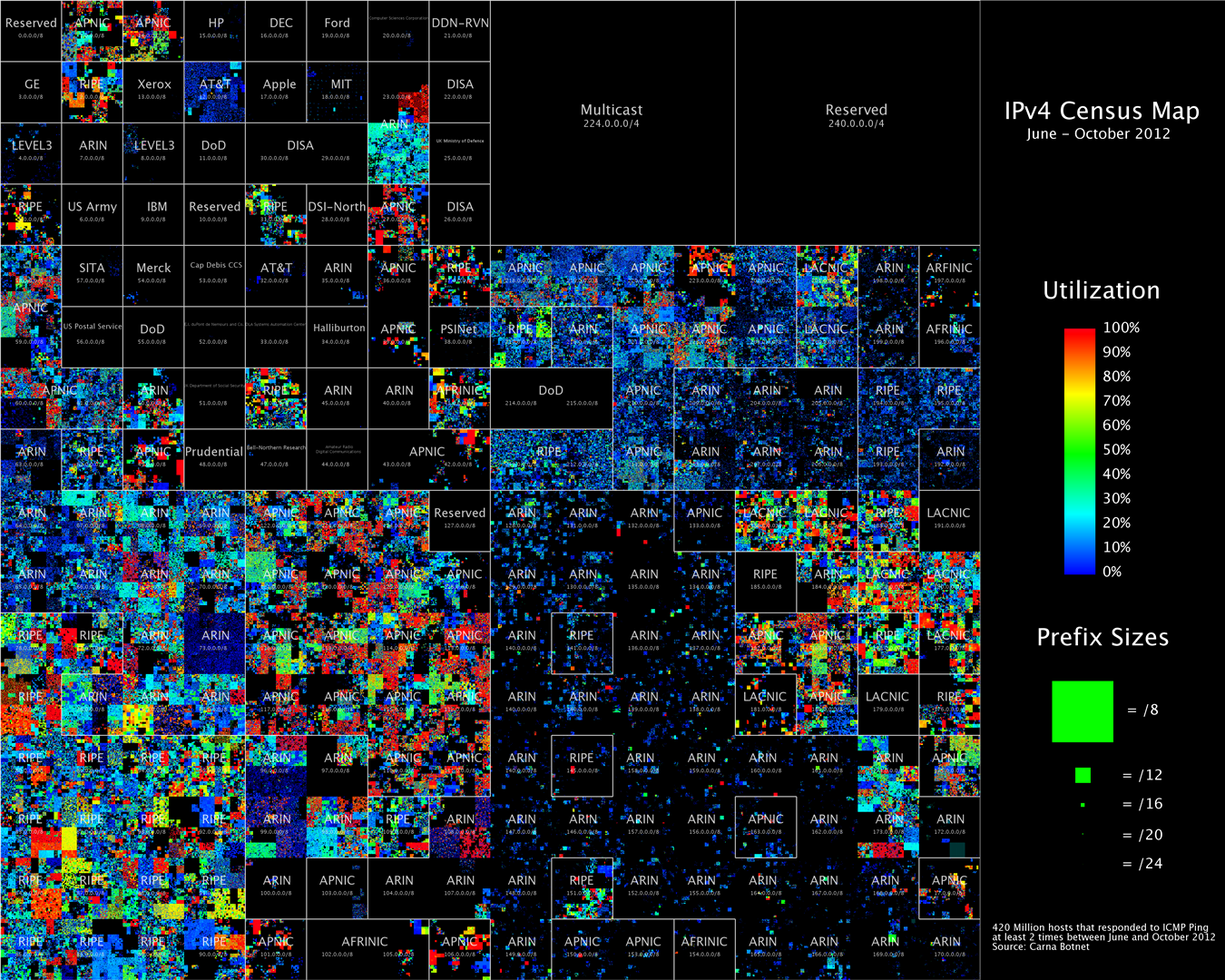
- You discovered that there are thousands of devices on the web with an easily exploitable vulnerability on them.
- The devices themselves can’t do much other than scan other devices and infect them with the same program.
- You decide to use them to map the entire internet just to see what is out there, and end up with a database of every IP and common open port on the internet.
Is that ethical? Is that legal?
Is that useful information?
Should you be put in jail for this?
Assignments
- Blog 12: Technology Company Profile - Due 11/30 10:00 PM
- Blog 13: Industry Speaker Response - Due 12/7 10:00 PM
- Mars Rover - Due 12/1 10:00 PM
- Video Project - Due 12/4 10:00 PM
- Scratch Game - Due 12/8 5:30 PM
- Blog 14: Where do I go from Here - Due 12/14 10:00 PM
Blog 13: Technology Company Profile
For this blog, choose a company that primarily works in the realm of technology, and tell us about that company. Some ideas you can use to start with:
- Why did you choose this company?
- What does this company do that is unique compared to others?
- Would you like to work at this company? Why?
- What is the history of this company? Have they always been doing what they are doing now?
- What products or services does this company provide that we would be familiar with?



















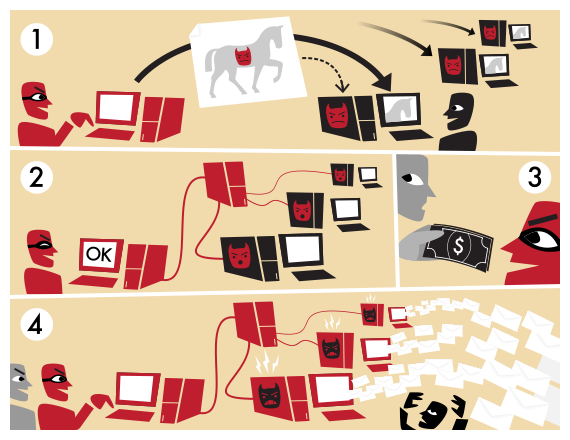


Social Engineering
Using techniques to compromise a system by exploiting the users directly instead of the system's security
Image Source: Wikipedia