CIS 115
Lecture 9: Cryptography
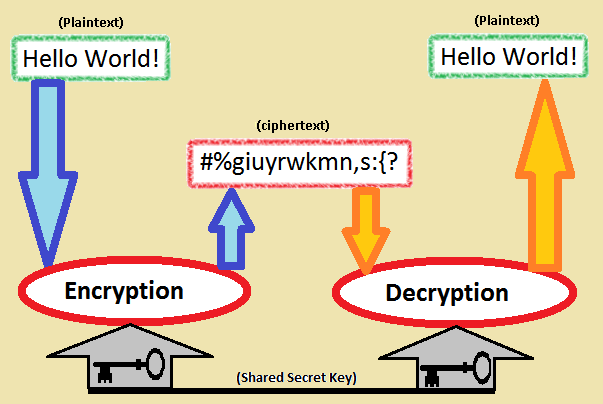
Cryptography
- Study of ways to communicate securely and privately in the presence of third parties
- Charles Babbage, Edgar Allan Poe, Alan Turing, and Claude Shannon were all involved in cryptography.
Message to the Class
TSTEPHAAXLISLAESCEMQIYQMessage to the Class
TSTEPHAAXLISLAESCEMQIYQT H I S I S A S C Y T A L E Q E X A M P L E QEarly Ciphers
- Substitution Ciphers
- Cryptoquip - Easily Breakable
- Polyalphabetic Ciphers
- First described by Al-Kindi in the 9th century
- Later explained by Leon Battista Alberti in 1467
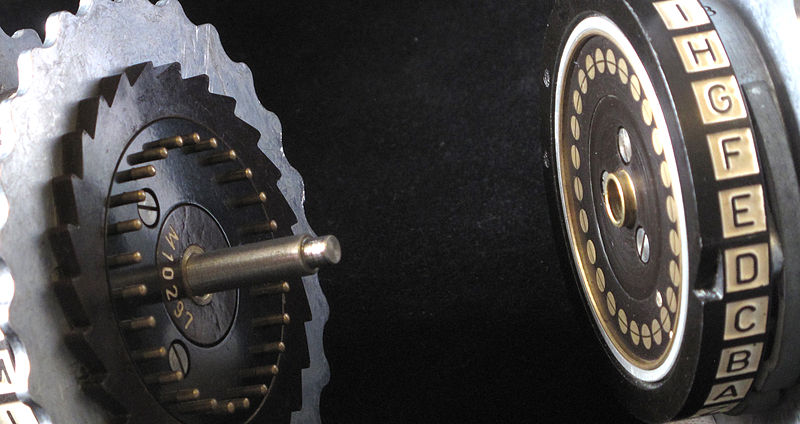
Image Source: Wikipedia

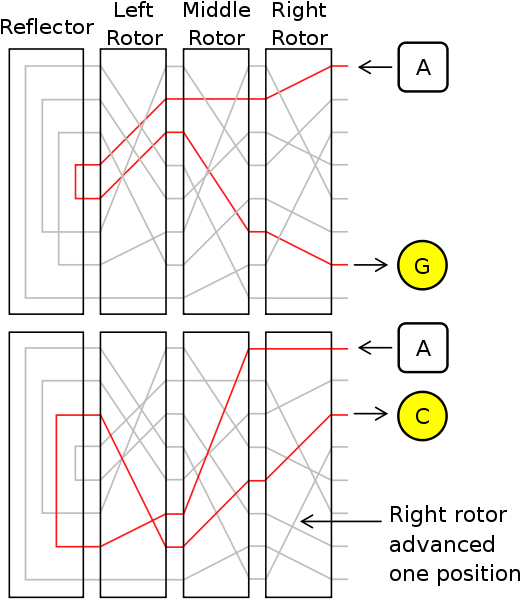
Image Source: Wikipedia
Enigma Key
- Choice and order of rotors
- Initial position of rotors
- Ring setting on rotors
- Plug connections
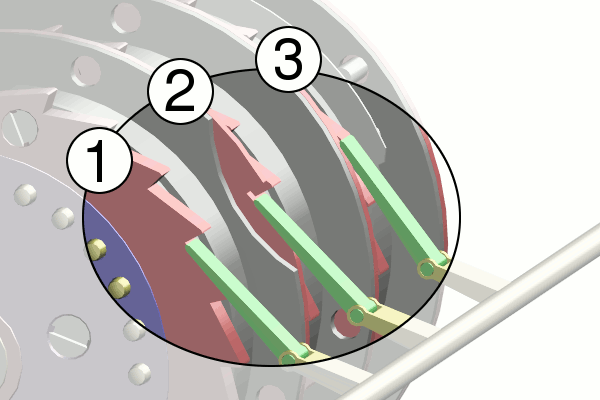
Enigma Operation
- Set wheels to today's key from codebook
- Operator chooses message key
- Encode message key TWICE to avoid errors
- Set wheels to message key
- Encrypt and send message
Enigma Stengths
- Many factors to the encryption
- Had up to 8 different wheels to choose from by the end of the war
- 150 Trillion different setups
Enigma Weaknesses
- A letter would never encrypt to itself
- Plugboards were reciprocal
- Wheels were not similar enough (could determine which wheels were used)
- Poor policies and procedures
Cracking Enigma
- 1932 - First cracked by Marian Rejewski of Poland
- 1938 - Germany added 2 wheels
- 1939 - Alan Turing creates Bombe
- 1945 - Almost every message deciphered within 2 days
Impact
“My own conclusion is that it shortened the war by not less than two years and probably by four years … we wouldn't in fact have been able to do the Normandy Landings, even if we had left the Mediterranean aside, until at the earliest 1946, probably a bit later.”
-Sir Harry Hinsley
British Intelligence Historian
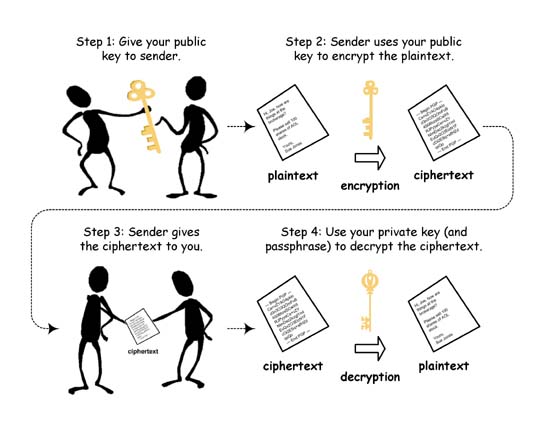
RSA Encryption
- Developed in 1977
- Named for the 3 creators (Ron Rivest, Adi Shamir, Lenonard Adleman)
- Uses the product of 2 large prime numbers to generate a key
- Key strength depends on the difficulty of factoring large numbers
RSA Example
- Choose 2 distinct prime numbers
p and q - Compute their product n = pq
- Compute the totient t of n:
t = (p - 1)(q - 1)
RSA Example
- Choose any number e less than t that is coprime to t (they share no common factors but 1)
- Calculate d as the modular multiplicative inverse of e (mod t)
e * x = 1 (mod t)
RSA Keys
- Public Key : (n, e)
- Encode: c = me (mod n)
- Private Key : (n, d)
- Decode: m = cd (mod n)
Assignments
- Read and be prepared to discuss:
- The Pattern on the Stone Chapter 9: Beyond Engineering
- Blog 4: Cryptography - Due 9/29 10:00 PM
- Scratch Sorting Project - Due 9/24 10:00 PM
- Scratch Chaocipher Project - Due 10/1 10:00 PM
Blog 4: Cryptography
Many systems today depend on cryptography that is assumed to be unbreakable with modern technology. However, imagine a world where that was no longer the case. Each time you purchase something on the internet, there would no longer be anything preventing someone from intercepting your information. The same would apply to sites such as Facebook, GMail, and even your banking or medical information. Anything you store on a computer could be accessed by anyone that wants to get it. Write about how you think that would affect our perception of technology and how we use it in our daily lives. Some thoughts to ponder:
- Would we stop shopping online, even if it is more convenient to do so?
- Would we be less likely to share information on social media sites?
- Would we insist that institutions such as banks or hospitals use only paper records, even though we understand that it will result in a rise in human errors?
- Are there uses of technology which are popular today that would disappear in this world? Or are there uses that would become much more common?
Scratch Chaocipher
- Download starter file from K-State Online
- Implement the missing parts of the chaochiper algorithm
- Test the program by encoding and decoding text
- Submit via K-State Online
- Due Tuesday, October 1 10:00 PM
Chaocipher
- Developed by J.F. Byrne in 1918
- Described in his 1953 autobiography
- Machine could fit in a cigar box
- Offered a reward to anyone who solved it
- Remained unsolved until 2010, when his papers were released posthumously by his family